攻防世界-密码学-root
题目信息
附件是一个流量包。
分析
在流量包中找到RSA公钥,由于没有提供任何其他信息,且模数位数很高,只能寄希望于因子之差很小,即采用费马攻击。之后将私钥导入流量包即可找出flag。
解题
解题的Python脚本如下:1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29from gmpy2 import isqrt,square,is_square
from Crypto.Util.number import *
from Crypto.PublicKey import RSA
def fermat_factors(n):
assert n % 2 != 0
a = isqrt(n)
b2 = square(a) - n
while not is_square(b2):
a += 1
b2 = square(a) - n
factor1 = a + isqrt(b2)
factor2 = a - isqrt(b2)
return int(factor1), int(factor2)
def solve():
N=0x726f6f7400000000000000000000000000000000001b000000000000000000000000001ffffb0000000000000000000000001ffffb0000000000000000000000001fffff7777777b00000000000000001ffffffffffffb00000000000000001ffffffffffb0000000000000000001ffffffffffb0000000000000000001ffffffffffffb00000000000000001fffff2222222b00000000000000001ffffb0000000000000000000000001ffffb0000000000000000000000001ffffb0000000000000000000000001ffffb0000000000000000000000001ffffb0000000000000000000000001ffffb0000000000000000000000001ffffb00000000000000265293c4422be3532638feeb2a635e865e5bccd4862d1491f8e46ed41afdab32ab1e913c296c45a723a371cc4ad218d273a494ac501a1c677576b84d3a1700b24e38f3d7c8090c952767f8a9da532eb4496a953fa2b2641f93af58321e491ad6b3e1f6600ea1757635a2d47562dff2f245bfc8ed511420931de246d56334d8897d6465b227f6c095ece1ad994c7551f08dbc21f8b40691ee51f5f72d052d9352062f90b0e7c52c2eb18196c2c985101af4eac67499396c6241ad4f2439ed11f87d67e73a239b865c45d65a61cf0f56082de831b97fb28ae8222a7195e0ec06c08281ffc16e7106e77e68b8c4510424beeb5582fe21cc345f53534682b75c368d73c9
E=31337
p,q=fermat_factors(N)
phi=(p-1)*(q-1)
assert GCD(E,phi)==1
d=inverse(E,phi)
rsakey=RSA.construct((N,E,d,p,q))
with open('key.pem','wb') as f:
f.write(rsakey.exportKey('PEM'))
return
if __name__=='__main__':
solve()
之后将私钥导入流量包,如下图所示:
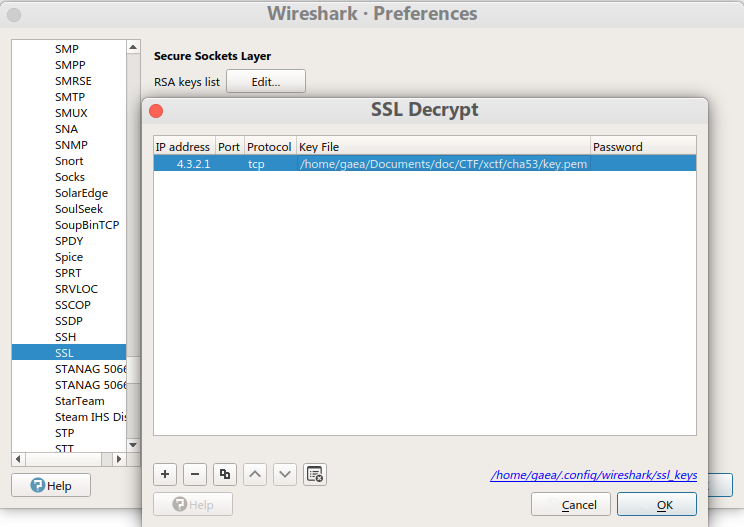
然后返回,快捷键Ctrl-Alt-Shift-S来追踪SSL流,在明文的最后以’666c6167’开头,而它正好是flag的16进制编码。将这串字符进行16进制解码即得到flag。1
2'666c61673a7768656e5f736f6c76696e675f70726f626c656d735f6469675f61745f7468655f726f6f74735f696e73746561645f6f665f6a7573745f6861636b696e675f61745f7468655f6c6561766573'.decode('hex')
'flag:when_solving_problems_dig_at_the_roots_instead_of_just_hacking_at_the_leaves'
